CWNA (Cisco Wireless Network Associate)
Radio
Frequency: Radio frequency is high frequency alternating current
(AC) signals that are passed along a copper conductor and then radiated into
the air via an antenna. An antenna converts/transforms a wired signal to a
wireless signal and vice versa. When the high frequency AC signal is radiated
into the air, it forms radio waves. These radio waves propagate (move) away
from the source (the antenna) in a straight line in all directions at once.
Antenna: Antennas
convert electrical energy into RF waves in the case of a transmitting antenna,
or RF waves into electrical energy in the case of a receiving antenna. The
physical dimensions of an antenna, such as its lenght, are directly related to the
frequency at which the antenna can propagate waves or receive propagated waves.
Bandwidth: Bandwidth
equal Frequency weight.
SSID
Information: Stations look in beacons for the SSID of the network they
wish to join. When this information is found, the station looks at the MAC
address of where the beacon originated and sends an authentication request in
hopes of associating with that access point.
If a station is set to accept any SSID, then the station will
attempt to join the network through the first access point that sends a beacon
or the one with the strongest signal strength if there are multiple access
points
Wireless
operation: Client and Access point Association:
- AP Signals: Beacon
- Client Signals: Probe
- Authentication: A. Open authentication. B. Share key authentication
- Association
Hop time: Hop time is
a time which is use between one frequency to another frequency, when jumping.
Dwell time: When
discussing frequency hopping systems, we are discussing systems that must transmit
on a specified frequency for a time, and then hop to a different frequency to
continue transmitting.
When a frequency hopping system transmits on a frequency, it
must do so for a specified amount of time. This time is called the dwell
time. Once the dwell time has expired, the system will switch to a
different frequency and begin to transmit again. Suppose a frequency hopping
system transmits on only two frequencies, 2.401 GHz and 2.402 GHz. The system
will transmit on the 2.401 GHz frequency for the duration of the dwell time—100
milliseconds (ms), for example.
After 100ms the radio must change its transmitter frequency
to 2.402 GHz and send information at that frequency for 100ms.
Co-location:
To use DSSS systems with overlapping channels in the same physical space
would cause interference between the systems. DSSS systems with overlapping
channels should not be co-located because there will almost always be a drastic
or complete reduction in throughput. Because the center frequencies are 5 MHz apart
and the channels are 22 MHz wide, channels should be co-located only if the
channel numbers are at least five apart: channels 1 and 6 do not overlap,
channels 2 and 7 do not overlap, etc. There is a maximum of three co-located
direct sequence systems possible because channels 1, 6 and 11 are the only
theoretically non-overlapping channels.
ISM and UNII Bands: The FCC
establishes rules limiting which frequencies wireless LANs can use and the
output power on each of those frequency bands. The FCC has specified that
wireless LANs can use the ISM (Industrial Scientific and Medical) bands, which
are license free. The ISM bands are located starting at 902 MHz, 2.4 GHz, and
5.8 GHz and vary in width from about 26 MHz to 150 MHz. In addition to the ISM
bands, the FCC specifies three Unlicensed National Information Infrastructure
(UNII) bands. Each one of these UNII bands is in the 5 GHz range and is 100 MHz
wide.
Unlicensed National Information Infrastructure (UNII) Bands:
The 5 GHz UNII bands are made up of three separate 100
MHz-wide bands, which are used by 802.11 -compliant devices. The three bands
are known as the lower, middle, and upper bands. Within each of these three
bands, there are four non-overlapping DSSS channels, each separated by 5 MHz.
The FCC mandates that the lower band be used indoors, the middle band be used
indoors or outdoors, and the upper band be allocated for outdoor use. Since
access points are mostly mounted indoors, the 5 GHz UNII bands would allow for
8 non-overlapping access points indoors using both the lower and middle.
Frequency
Hopping Spread Spectrum (FHSS): Frequency hopping spread spectrum
is a spread spectrum technique that uses frequency agility to spread the data
over more than 83 MHz. Frequency agility refers to the radio’s ability to
change transmission frequency abruptly within the usable RF frequency band. In
the case of frequency hopping wireless LANs, the usable portion of the 2.4 GHz
ISM band is 83.5 MHz, per FCC regulation and the IEEE 802.11 standard.
Direct Sequence
Spread Spectrum (DSSS): Direct sequence spread spectrum is very widely known and the most used
of the spread spectrum types, owing most of its popularity to its ease of implementation
and high data rates. The majority of wireless LAN equipment on the market today
uses DSSS technology. DSSS is a method of sending data in which the
transmitting and receiving systems are both on a 22 MHz-wide set of
frequencies. The wide channel
enables devices to transmit more information at a higher data rate than current
FHSS systems.
Direct
Sequence Systems
In the 2.4 GHz ISM band, the IEEE specifies the use of DSSS
at a data rate of 1 or 2Mbps under the 802.11 standard. Under the 802.11b
standard—sometimes called high rate wireless—data rates of 5.5 and 11 Mbps are
specified. IEEE 802.11b devices operating at 5.5 or 11 Mbps are able to
communicate with 802.11 devices operating at 1 or 2 Mbps because the 802.11b
standard provides for backward compatibility. A recent addition to the list of
devices using direct sequence technology is the IEEE 802.11a standard, which
specifies units that can operate at up to 54 Mbps. Unfortunately , 802.11a is wholly
incompatible with 802.11b because it does not use the 2.4 GHz band, but instead
uses the 5 GHz UNII bands. Recently the IEEE 802.11g standard was approved to
specify direct sequence systems operating in the 2.4 GHz ISM band that can
deliver up to 54 Mbps data rate. The 802.11g technology became the first 54
Mbps technology that was backward compatible with 802.11 and 802.11b devices.
WLAN Standards: The Institute of
Electrical and Electronics Engineers (IEEE) is the key standards maker
for most things related to information technology in the United States. The
IEEE creates its standards within the laws created by the FCC. The IEEE
specifies many technology standards such as Public Key Cryptography (IEEE
1363), Ethernet (IEEE 802.3), and Wireless LANs (IEEE 802.11). It is part of
the mission of the IEEE to develop standards for wireless LAN operation within
the framework
of the FCC rules and regulations. Following are the four main IEEE standards
for WLAN.
- IEEE 802.11
- IEEE 802.11b
- IEEE 802.11a
- IEEE 802.11g
- IEEE 802.11n
- IEEE 802.11e
802.11 compliant products operate
strictly in the 2.4 GHz ISM band between 2.4000 and 2.4835 GHz. Infrared, also
covered by 802.11, is light-based technology and does not fall into the 2.4 GHz
ISM band.
IEEE 802.11b: DSSS
systems that operate at 1, 2, 5.5 and 11 Mbps. The 802.11b standard does not
describe any FHSS systems. 802.11b-compliant devices are also
802.11-compliant by default, meaning they are backward compatible and support
both 2 and 1 Mbps data rates. Backward compatibility is very important because
it allows a wireless LAN to be upgraded without the cost of replacing the core
hardware.
IEEE 802.11a: Describe
WLAN operation in the “UNII” band. Operation in a different frequency band.
Compatibale with 802.11b, 5GHz frequency band. Max data rate of 54Mbps
(Typically 20-25Mbps), 12 Non-overlapping chanels, 8 outdor, 4 PTP.
IEEE 802.11g: 802.11g
provides the same maximum speed of 802.11a, coupled with backwards compatibility
for 802.11b devices. This backwards compatibility will make upgrading wireless
LANs simple and inexpensive. IEEE 802.11g specifies operation in the 2.4 GHz
ISM band. To achieve the higher data rates found in 802.11a, 802.11g compliant
devices utilize Orthogonal Frequency Division Multiplexing (OFDM) modulation
technology. These devices can automatically switch to QPSK modulation in order
to communicate with the slower 802.11b- and 802.11-compatable devices.
IEEE 802.11n: IEEE
802.11n-2009, commonly shortened to 802.11n, is a wireless networking standard
that uses multiple antennas to increase data rates. It is an amendment to the
IEEE 802.11-2007 wireless networking standard. Its purpose is to improve
network throughput over the two previous standards—802.11a and 802.11g—with a
significant increase in the maximum net data rate from 54 Mbit/s to 600 Mbit/s.
with the use of four spatial streams at a channel width of 40 MHz. 802.11n
standardized support for multiple-input multiple-output and frame aggregation,
and security improvements, among other features. It can be used in the 2.4 GHz
or 5 GHz frequency bands.
WIMAX Technology: IEEE
802.16e standard broadband wireless access (BWA) working group.
Blutooth Technology: IEEE
802.15.1 Standard.
RF
Behaviors
Loss: Loss describes a decrease in
signal strength. Many things can cause RF signal loss, both while the signal is
still in the cable as a high frequency AC electrical signal and when the signal
is propagated as radio waves through the air by the antenna.
Resistance of cables and connectors
causes loss due to the converting of the AC signal to heat. Impedance
mismatches in the cables and connectors can cause power to be reflected back
toward the source, which can cause signal degradation. Objects directly in the
propagated wave's transmission path can absorb, reflect, or destroy RF signals.
Loss can be intentionally injected into a circuit with an RF attenuator. RF
attenuators are accurate resistors that convert high frequency AC to heat in
order to reduce signal amplitude at that point in the circuit.
Gain: Gain is the term used to
describe an increase in an RF signal's amplitude. Gain is usually an active
process; meaning that an external power source, such as an RF amplifier, is
used to amplify the signal or a high-gain antenna is used to focus the
beamwidth of a signal to increase its signal amplitude.
Reflection: Reflection
occurs when a propagating electromagnetic wave impinges upon an object that has
very large dimensions when compared to the wavelength of the propagating wave.
Reflections occur from the surface of the earth, buildings, walls, and many
other obstacles. RF signal reflection can cause serious problems for wireless
LANs. This reflecting of the main signal from many objects in the area of the
transmission is referred to as multipath.
Multipath can have severe adverse affects on a
wireless LAN, such as degrading or, canceling the main signal and causing holes
or gaps in the RF coverage area. Surfaces such as lakes, metal roofs, metal
blinds, metal doors, and others can cause severe reflection, and hence,
multipath. Reflection of this magnitude is never desirable and typically requires special functionality (antenna diversity)
within the wireless LAN hardware to compensate for it.
Refraction: Refraction
describes the bending of a radio wave as it passes through a medium of different
density. As an RF wave passes into a denser medium (like a pool of cold air
lying in a valley) the wave will be bent such that its direction changes. When
passing through such a medium, some of the wave will be reflected away from the
intended signal path, and some will be bent through the medium in another
direction.
Diffraction: Diffraction
occurs when the radio path between the transmitter and receiver is obstructed
by a surface that has sharp irregularities or an otherwise rough surface. At
high frequencies, diffraction, like reflection, depends on the geometry of the
obstructing object and the amplitude, phase, and polarization of the incident
wave at the point of diffraction.
Scattering: Scattering
occurs when the medium through which the wave travels consists of objects with
dimensions that are small compared to the wavelength of the signal, and the
number of obstacles per unit volume is large. Scattered waves are produced by
rough surfaces, small objects, or by other irregularities in the signal path.
Voltage Standing Wave Ratio (VSWR): VSWR occurs when there is mismatched impedance (resistance to
current flow, measured in Ohms) between devices in an RF system. VSWR is caused
by an RF signal reflected at a point of impedance mismatch in the signal path.
VSWR causes return loss,
which is defined as the loss of forward energy through a system due to some of
the power being reflected back towards the transmitter. If the impedances of
the ends of a connection do not match, then the maximum amount of the
transmitted power will not be received at the antenna. When part of the RF
signal is reflected back toward the transmitter, the signal level on the line
varies instead of being steady. This variance is an indicator of VSWR.
Line of Sight (LOS):
With visible light, visual LOS (also called simply ‘LOS’) is defined as
the apparently straight line from the object in sight (the transmitter) to the
observer's eye (the receiver). The LOS is an apparently straight line
because light waves are subject to changes in direction due to refraction, diffraction, and reflection in the same
way as RF frequencies.Fresnel Zone:
The Fresnel Zone occupies a series of concentric ellipsoid-shaped areas around the LOS path, The Fresnel Zone is important to the integrity of the RF link because it defines an area around the LOS that can introduce RF signal interference. if blocked. Objects in the Fresnel Zone such as trees, hilltops, and buildings can diffract or reflect the main signal away from the receiver, changing the RF LOS. These same objects can absorb or scatter the main RF signal, causing degradation or complete signal loss.
WLAN Infrastructure Devices
Access
Point: The access point, or “AP”, is probably the most common
wireless LAN device with which you will work as a wireless LAN administrator.
As its name suggests, the access point provides clients with a point of access
into a network. An access point is a half-duplex device with intelligence
equivalent to that of a sophisticated Ethernet switch.
Access Point Modes: Access
points communicate with their wireless clients, with the wired network, and
with other access points. There are three modes in which an access point can be
configured:
- Root Mode
- Repeater Mode
- Bridge Mode
Root Mode: Root Mode
is used when the access point is connected to a wired backbone through its
wired interface. Most access points that
support modes other than root mode come configured in root mode by default.
When an access point is connected to the wired segment through its Ethernet
port, it will normally be configured for root mode. When in root mode, access
points that are connected to the same wired distribution system can talk to
each other over the wired segment. Access points talk to each other to
coordinate roaming functionality such as reassociation. Wireless clients can
communicate with other wireless clients that are located in different cells
through their respective access points across the wired segment.
Bridge Mode: In bridge
mode, access points act exactly like wireless bridges. In fact, they become
wireless bridges while configured in this manner.
Repeater Mode:
In repeater mode, access points
have the ability to provide a wireless upstream link into the wired network rather
than the normal wired link. One access point serves as the root access point
and the other serves as a wireless repeater. The access point in repeater mode
connects to clients as an access point and connects to the upstream root access
point as a client itself. Using an access point in repeater mode is not
suggested unless absolutely necessary because cells around each access point in
this scenario must overlap by a minimum of 50%. Additionally, the repeater
access point is communicating with the clients as well as the upstream access
point over the wireless link, reducing throughput on the wireless segment.
Users attached to the repeater access point will likely experience low
throughput and high latencies in this scenario.
Scanning: When you install, configure, and finally start up a wireless LAN client
device the client will automatically “listen" to see if there is a
wireless LAN within range. The client is also discovering if it can associate
with that wireless LAN. This process of listening is called scanning. Scanning
occurs before any other process, since scanning is how the client finds the
network.
Passive Scanning: Passive scanning is the process of listening
for beacons on each channel for a specific period of time after the station is
initialized. These beacons are sent by access points (infrastructure mode) or
client stations (ad hoc mode), and the scanning station catalogs characteristics
about the access points or stations based on these beacons. The station
searching for a network listens for beacons until it hears a beacon listing the
SSID of the network it wishes to join. The station then attempts to join the
network through the access point that sent the beacon. In configurations where
there are multiple access points, the SSID of the network the station wishes to
join may be broadcast by more than one of these access points. In this
situation, the station will attempt to join the network through the
access point with the strongest signal strength and the lowest bit error rate. Stations continue passive scanning even after associating to
an access point. Passive scanning saves time reconnecting to the network if the
client is disconnected (disassociated) from the access point to which the
client is currently connected. By maintaining a list of available access points
and their characteristics (channel, signal strength, SSID, etc), the station
can quickly locate the best access point should its current connection be
broken for any reason. Stations will roam from one access point to another
after the radio signal from the access point where the station is connected
gets to a certain low level of signal strength. Roaming is implemented so that
the station can stay connected to the network. Stations use the information
obtained through passive scanning for locating the next best access point (or
ad hoc network) to use for connectivity back into the network. For this reason, overlap between access point cells is
usually specified at approximately 20-30%. This overlap allows stations to
seamlessly roam between access points while disconnecting and reconnecting
without the user’s knowledge.
Active
scanning: Active scanning involves the sending of a probe request frame
from a wireless station. Stations send this probe frame when they are actively
seeking a network to join. The probe frame will contain either the SSID of the
network they wish to join or a broadcast SSID. If a probe request is sent
specifying an SSID, then only access points that are servicing that SSID will
respond with a probe response frame. If a probe request frame is sent with a
broadcast SSID, then all access points within reach will respond with a probe
response frame. The point of probing in this manner is to locate access
points through which the station can attach to the network. Once an access
point with the proper SSID is found, the station initiates the authentication
and association steps of joining the network through that access point.
Authentication & Association: The process
of connecting to a wireless LAN consists of two separate sub-processes. These
sub-processes always occur in the same order, and are called authentication and
association. For example, when we speak of a wireless PC card connecting to a wireless LAN, we say that the PC card has
been authenticated by and has associated with a certain access point.
Authentication: The first
step in connecting to a wireless LAN is authentication. Authentication is the
process through which a wireless node (PC Card, USB Client, etc.) has its
identity verified by the network (usually the access point) to which the node
is attempting to connect.
This verification occurs when the
access point to which the client is connecting verifies that the client is who
it says it is.
Association: Once a
wireless client has been authenticated, the client then associates with the
access point. Associated is the state at which a client is allowed to
pass data through an access point.
If your PC card is associated to an
access point, you are connected to that access point, and hence, the network. The
process of becoming associated is as follows. When a client wishes to connect,
the client sends an authentication request to the access point and receives
back an authentication response. After authentication is completed, the station
sends an association request frame to the access point who replies to the client
with an association response frame either allowing or disallowing association.
WLAN
Applications
Access Role: Wireless
LANs are deployed in an access layer role, meaning that they are used as an
entry point into a wired network. In the past, access has been defined as
dial-up, ADSL, cable, cellular, Ethernet, Token Ring, Frame Relay, ATM, etc.
Wireless is simply another method for users to access the network. Wireless
LANs are Data-Link layer networks like all of the access methods.
Network
Extension: Wireless networks can serve as an extension to a wired
network. There may be cases where extending the network would require
installing additional cabling that is cost prohibitive. You may discover that
hiring cable installers and electricians to build out a new section of office
space for the network is going to cost tens of thousands of dollars. In the case of a large warehouse, the distances
may be too great to use Category 5. Fiber might have to be installed, requiring
an even greater investment of time and resources. Installing fiber might
involve upgrades to existing edge switches.
Building-to-Building Connectivity (Point to Point):
In a campus environment or an environment with as few as two
adjacent buildings, there may be a need to have the network users in each of
the different buildings have direct access to the same computer network. In the
past, this type of access and connectivity would be accomplished by running
cables underground from one building to another or by renting expensive
leased-lines from a local telephone company. Using wireless LAN technology,
equipment can be installed easily and quickly to allow two or more buildings to
be part of the same network without the expense of leased lines or the need to
dig up the ground between buildings. There are two different types of
building-to-building connectivity. The first is called point-to-point (PTP),
and the second is called point-to-multipoint (PTMP). Point-to-point links are
wireless connections between only two buildings.
Building-to-Building Connectivity (Point to Multipoint):
Last Mile Data Delivery: Wireless
Internet Service Providers (WISPs) are now taking advantage of recent
advancements in wireless technology to offer last mile data delivery service to
their customers. "Last mile" refers to the communication
infrastructure—wired or wireless that exists between the central office of the
telecommunications company (telco) or cable company and the end user.
Service Sets
A service set is a term used to describe the basic
components of a fully operational wireless LAN. There are three ways to
configure a wireless LAN, and each way requires a different set of hardware.
The three ways to configure a wireless LAN are:
- Independent Basic Service Set (IBSS)
- Basic Service Set (BSS)
- Extended Service Set (ESS)
Independent Basic Service Set (IBSS):
An independent basic service set is also known as an ad
hoc network. An IBSS has no access point or any other access to a
distribution system, but covers one single cell and has one SSID. The clients
in an IBSS alternate the responsibility of sending beacons since there is no
access point to perform this task. In order to transmit data outside an
IBSS, one of the clients in the IBSS must be acting as a gateway, or router,
using a software solution for this purpose. In an IBSS, clients make direct
connections to each other when transmitting data, and for this reason, an IBSS
is often referred to as a peer-to-peer network.
Basic Service Set (BSS):
When one access point is connected to a wired network and a
set of wireless stations, the network configuration is referred to as a basic
service set (BSS). A basic service set consists of only one access point and
one or more wireless clients.
A basic service set uses infrastructure mode - a mode
that requires use of an access point and in which all of the wireless traffic
traverses the access point. No direct client-to-client transmissions are
allowed.
Each wireless client must use the access point to communicate
with any other wireless client or any wired host on the network. The BSS covers
a single cell, or RF area, around the access.
Extended Service Set (ESS):
An extended service set is defined as two or more basic
service sets connected by a common distribution system. The distribution system
can be either wired, wireless, LAN, WAN, or any other method of network
connectivity. An ESS must have at least 2 access points operating in
infrastructure mode. Similar to a BSS, all packets in an ESS must go through
one of the access points.
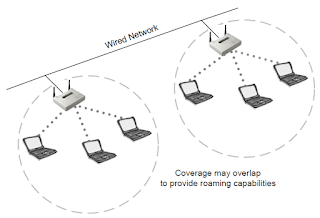
Roaming: Roaming is the process or ability of a
wireless client to move seamlessly from one cell (or BSS) to another without
losing network connectivity. Access points hand the client off from one to
another in a way that is invisible to the client, ensuring unbroken
connectivity. When any area in the building is within reception range of more
than one access point, the cells’ coverage overlaps. Overlapping coverage areas
are an important attribute of the wireless LAN setup, because it enables
seamless roaming between overlapping cells. Roaming allows mobile users with
portable stations to move freely between
overlapping cells, constantly maintaining their network connection. Note: when roaming, we perform 15% to 20% overlapping.
Overlapping:
On co-location overlapping occure, to avoid ovelapping we must change the
channels.
IBSS
Lab1_Software
based Bridge:
Step1: On PC1 >
network and sharing center > manage wireless network > click on Add
button (to create folder for WLAN profile for Ad-hoc mode) > click on Ad-hoc
network > next > network name (SSID): Ad-hoc-test, security type: wep,
security key: 123abc > next > next > close.
Step2: On PC2,
PC3, and PC4 > Right click on network icon on task bar > now connect to
Ad-hoc-test > give password > ok.
Step3: On PC1 >
open network and sharing center > change adapter settings > merge both
Local area connection and wireless network connection > select both >
right click > Bridge connections > ok > right click on wireless
network connection > properties > give IP, Gateway and DNS if not get
> ok.
Now we created software based Bridge from PC1, and when PC2,
PC3, PC4 wants to access Internet it will success.
Lab2_Internet
connection sharing (in Ad-hoc mode):
Small office and home office, we can use ICS in ad-hoc mode.
In windows ICS is the process of sharing a single Internet connection (DSL)
between multiple users. A number of technologies use involved in ICS. For
example: NAT, Baby DHCP, Basic Firewall, Cash DNS, Proxy server.
On wired
network:
Step1: Install two
link cards on ICS Server, and configure the link card which is connected to
DSL.
Step2: Right click
on the NIC which is connected to DSL > properties > sharing > check
Allow other network users to connect through this computer Internet connection
> ok > setting > Allow FTP, Telnet, etc.
Note: when we share Internet connection through ICS, the IP
address format will be 192.168.137.any.
ICS on wired network:
ICS on wireless network:
Or:
BSS
Lab3_Creating
a simple wireless network (single AP):
Step1: Connect to
AP using web interface (every AP have builtin web server for configuration)
> Internet explorer > http://192.168.1.1 > enter
> username: admin, password: admin > enter.
Step2: Network
> change IP address here (give any IP) > Wireless settings > basic
settin > SSID: test, Region: Afghanistan, Channel: 11, Mode: 54Mbps
(802.11g) > save.
Note: if we have same vendor equipements select propritary
speeds mode.
ESS
Lab4_Creating
two AP with roaming:
Step1: Connect to
AP1 through web browser > http://192.168.1.1 > enter
> username: admin, password: admin > ok.
Step2: Network tab
> change IP address > save > Wireless tab > Basic settings >
SSID: ccna, Region: Afghanistan, channel: 6, Mode: 54Mbps (802.11g) > save.
Step3: Connect to
AP2 through web browser > http://192.168.1.1 > enter
> username: admin, password: admin > ok.
Step4: Wireless
tab > Basic settings > SSID: ccna, Region: Afghanistan, Channel: 1, Mode:
54Mbps (802.11g) > save. Now connect PCs to AP.
Note: on roaming cause we must overlapping 20%, and SSID and
password of both AP wil be same and channels will be different.
Channels 1,3,6,7,11 are none overlapping channels. 1,6,11
channels are free channels.
Lab5_Configuring
AP as DHCP Server:
Step1: Connect to
AP > DHCP > Enable, give start IP, end IP, and reserved > save >
manual reboot > System tools > Reboot > ok.
Note: In LAN we give IP time 7 days (optional), but in
wireless network we mention as 8 hours (optional).
Lab6_Wireless
station isolation:
We enable wireless station isolation/AP isolation, where
students and visitors are resides.
AP isolation restricts WLAN station from accessing each other
through WLAN.
Step1: Connect to
AP > Wireless settings tab > check Enable AP isolation > save > ok.
Now ping between clients it will not access each other.
Lab7_Mac
Filtering:
Using Mac filtering, we can
restrict unauthorized users/machines form connecting to the WLAN. AP
operates at the data link layer and physical layer, so it can filter based on
physical/Mac address.
Step1: Connect to
AP > Wireless tab > wireless mac filtering > select Deny the stations
not spesified by any enabled entries in the list to access > click on Enable
> Ad new > give here Mac address of PCs that you want to allow > save
> ok.
Lab8_Wireless
Bridge mode (Point to Point):
Step1: Connect to
AP1 using web browser > wireless tab > wireless mode > select Bridge
(Point to Point), Now click on survey button to scan all Access points Mac
address, on survey page select AP2 Mac address and connect or give manually AP2
Mac address > save.
Step2: Connect to
AP2 using web browser > Wireless tab > wireless mode > select Bridge
(Point to Point), Now give Mac of AP1 > save.
Note: In this
case SSID and channel will be same. If we want to connect users then we select
Bridge+AP mode.
Lab9_Wireless
Bridge mode (Point to Multipoint):
Step1: Configure
Point to Multipoint Bridge > connect to AP1 (Point to Multipoint Bridge)
> wireless > wireless mode > Bridge (Point to Multipoint), here
mention other two AP’s Mac addresses
> next > save > ok.
Step2: Connect to
AP2 (Point to Point Bridge) > wireless > wireless mode > select Bridge
(Point to Point), here give AP1 Mac address > save > ok.
Step3: Connect to
AP3 (Point to Point Bridge) > wireless > wireless mode > select Bridge
(Point to Point), here give AP1 Mac address > save > ok.
Lab10_Repeater
Mode:
Repeater receives a wireless signal, regenrates the signal
and then send it forward destination network.
Step1: Configure
AP1 in Root mode > connect to the AP1 > wireless > wireless mode >
select Access Point, Enable SSID broadcast > save > ok.
Step2: configure
AP2 as Repeater > Connect to AP2 > wireless > wireless mode >
select Repeater, give Mac address of AP1 > save > ok.
Wireles network:
Lab11_External
Access Point (CPE):
CPE is use for external WLAN installation. Ex: In campus
network.
Step1: Connect to
E.AP (default IP 192.168.1.254, username: admin, password: admin) > network
> give IP, subnet mask, gateway > save. > wireless tab > Basic
setting > SSID: IT-Switcher, Region: pakistan, channel: 6, power: 27DBm Max
(600m), or 24, 21, 18, 15 it is Radiation power > Mode: 54Mbps (802.11g)
> save.
Wireless tab > wireless mode > Access point > save.
Lab12_E.AP
Repeater mode:
Step1: Connect to
E.AP > wireless > wireless mode > Repeater, give Mac address of AP
> save.
Step2: Connect to
AP > wireless > wireless mode > Access Point, Mac of E.AP(repeater)
> save.
Lab13_E.AP+DHCP
Server:
Step1: Connect to
AP > advance setting > DHCP > Enable, static, end IP, address lease
time, gateway, DNS > save > reboot (to reboot go to tools > reboot
> reboot > ok.
Wireless CPE modes
AP Client router, AP router, AP.
Lab14_Configuring
external CPE as a WISP client router:
Step1: Connect to
the External CPE through web browser > username and password > Quick
setup > next > select AP client router > next > select PPPoE >
next > give username and password which are given by WISP > next >
finish. OR,
Quick setup > next > select AP client router > next
> Dynamic > next > SSID: Linkwisp (which are provided by wisp) >
next > finish. Now we assign dynamically IP, Username, and Password. OR,
Quick setup > next > select AP client router > next
> Static > next > give IP, SSID, Username, and Password which are
given by WISP > next > finish.
Lab15_Configuring
External CPE as AP Router:
Step1: Connect to
E.AP through web browser > Quick setup > next > select AP Router >
next > select PPPoE > next > give username and password (which are
given by WISP) > next > SSID, Region , Channel, Mode, (For LAN) > next
> finish.
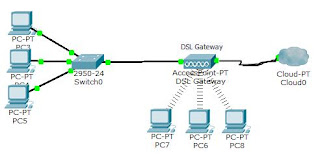
Wireless
Gateway (DSL):
A Gateway for router is a network device which allows
communication of packets between networks. This is a difference between a
gateway of router.
Gateway operates at all layer of OSI models, Router operates
on Physical, Datalink, and Network layers.
Lab16_Configuring
wireless gateway for Internet access:
Step1: Configure Internet settings (Ips settings).
Step2: Configure LAN IP settings.
Step3: Configuring DHCP for LAN clients.
Step4: Configuring SSID (WLAN) for WLAN settings.
Step1: Configure
Internet settings (IP settings) > Connect to e1000 gateway through web
browser > http://192.168.1.1 > enter
> username and password > Setup > Basic setup > select Static IP,
Internet IP, Gateway (DSL) > next > Network setup (LAN) > IP address:
172.16.10.1 > save > ok. Note: In LAN now we give static IP to PCs.
Step2: Configure
DHCP > DHCP server > Enable > give start and end IP, client lease time
(120) minuts > save.
Step3: Configure
WLAN for WLAN stations > Wireless tab > Configuration view, Manual >
network mode: Mixed, Network name (SSID): free-wlan, channel: 11, SSID: Enabled
> save > ok.
Lab17_Mac
filtering (Gateway):
Step1: Connect to
Gateway > Wireless tab > Wireless Mac filter > Enable > select
Permit PCs listed below to access the wireless network, (here we give Mac
addresses of PCs and these will be allowed other all will be denied) > save.
Lab18_Access
Restrictions (only in gateway and CISCO wireless routers):
Internet
Access restriction: is a limited level Firewall, allows to create Internet
access policies. Each policy can have a no of conditions:
- The list of computers to which the policy applies
- The schedule during which the policy is applicable (day+time restrictions)
- URLs either allowed or denied (www.facebook.com)
- Website either allowed or blocked based on regulas expression or keyword
- Blocked Applications
- Port or port range
Define Internet access policies, we have three policies: 1.
No Internet/network access, 2. Internet access, 3. Internet access for specific
group.
Step1: Connect to gateway
> Access Restrictions > Internet access policy > Access policy: 1,
Access restriction: Deny schedule: Everyday, applied
PCs: edit, here we give range of PCs to implement this policy, > save >
ok.
Step2: Connect to
Gateway > Access Restrictions > Internet access for all in break time:
access policy: 2, > access restrictions > access restriction : Allow,
schedule: Everyday, Time: 12PM to 02PM, website blocking by keyword: Keyword1:
Tube, Keyword2: adult > URL1: www.facebook.com, blocked
applications: select here applications that you want to block: Telnet, Ping,
FTP, etc > Apply PCs: Edit list, give here IP range which you want to apply
this policy > save > ok.
Step3: For
managers Internet access: access policy: 3, Access restriction > Access
Restriction: Allow: Everyday, Time: 8AM to 4PM, Enter policy name: Managers
> Eanabled, > save > ok.
Wireless Network Security
Two types
of Access Point:
- Simple Access point: in simple Access point we can’t block any URL or Key words
- Router Access point: in router Access point we can block any URL and key words
Wireless Print Server
Lab19_Configuring
wireless Print Server (Ad-hoc mode):
Step1: Connect to
the wireless Print server through wireless (in Ad-hoc) > click on wireless
icon adn select WLAN-PS > connect > ok.
Step2: Open
network and sharing center > click on wireless network connection > Properties
> Ipv4 > properties: 192.168.0.20 > ok. Now Ping to 192.168.0.10.
Step3: Connect to
the wireless Print server > Internet explorer > username, password >
Setup: system (form here we change name and user name password) > save and
restart.
Step4: Setup:
wireless > network type (Ad-hoc), SSID: WLAN, Channel: 11, Transmission
rate: Auto, wireless mode: B/G mixed > advanced settings: securityu tupe
> Wep > key index: 1, Encryption type: 64bit, key: 123, Authentication:
shared > save.
Installing Print
Server: Insert
Print server software CD to CDROM > run > click on wireless Print server
> setup wizard > next > select wireless print server > next >
Yes... > password of Print server > next > Communication type: Ad-hoc
> next > give security > next > give IP > next
> next > add new printer ( Printer drive) > add a local printer >
select Printer > next > next > finish.
Note: now we send jobs to Print server on which Printer
driver and software of Print server installed. If we want to send jobs from
other clients direct, then we must install Printer driver and Print server
software.
Note2: if we want to install Printer in infrastructure mode,
then we must connect Print server with access Pointy.
Lab20_Configuring
wireless Print server in infrastructure mode:
Step1: Install
Printer driver on the Print server.
Step2: Configure
the wireless Print server > connect to WLAN Print server using web browser
> http://192.168.0.10 > user:
admin, password: 123@qwe > setup, wireless > network type:
Infrastructure, Channel: 1, SSID: CCNA, > save. (channel and SSID of AP).
Step3: Print
server > run the software CD > select wireless Printer > next >
........ > finish.
End...


































No comments:
Post a Comment